WHAT WE KNOW ABOUT THE EQUIFAX BREACH
On September 7th, credit reporting agency Equifax announced “a cybersecurity incident potentially impacting approximately 143 million U.S. consumers.” To put this in context, at this time, this incident is almost seven times larger than the Office of Personnel Management breach of 2015. Equifax discovered the unauthorized access on July 29th and determined that the intrusion began in mid-May. Equifax stated that “the information accessed primarily includes names, Social Security Numbers (SSNs), birth dates, addresses and, in some instances, driver’s license numbers. In addition, credit card numbers for approximately 209,000 U.S. consumers, and certain dispute documents with personal identifying information for approximately 182,000 U.S. consumers, were accessed.” In addition, the “limited personal information” for Canadian and United Kingdom citizens was all accessed. The initial attack vector was reported as a “web application vulnerability.”

WHAT WE DON’T KNOW ABOUT THE EQUIFAX BREACH
Whenever doing any sort of analysis, it is important to state what we don’t know. Simply put there is a great deal we don’t know and most of the public will never know (despite what some talking heads might claim). As a former incident responder, I know that investigations aren’t completed in the time it takes to complete an episode of TV drama Scorpion. (Did you know that Scorpion is starting its fourth season?) Equifax stated that the investigation is “substantially complete,” but wisely added that “it remains ongoing and is expected to be completed in the coming weeks.”
- We don’t actually know how many SSNs were compromised.
- We don’t know if all 143 million individual’s SSNs were impacted.
- We don’t know the threat actor responsible for this intrusion. Equifax claimed that “criminals exploited” a web application, but attribution is always a challenge. Structured Analytic Techniques, like the Analysis of Competing Hypothesis we did for WannaCry, can be useful for considering attribution.
- Speaking of web applications, although we don’t know the specific vulnerability that was exploited, I’d bet 1,000 Gold Dragons it was SQL injection.
WHAT IS MOST LIKELY TO HAPPEN NEXT
There are a wide range of possibilities depending on the goals of the threat actor responsible for the Equifax intrusion. By the way, did I mention that attribution is challenging? Attribution aside, one thing is certain though, regardless of the motivations of the attackers, this data is perfect for social engineering attacks.
Tax Return Fraud
SSNs are highly valuable for criminals looking to commit tax refund fraud. Fraudsters use SSNs to file a tax return claiming a fraudulent refund and it can be hard to find out if you’re a victim until it is too late. There is some good advice from the IRS about what to do should you suffer from this form of fraud. You can read more about tax fraud in a blog we wrote earlier this year.
Opening Fraudulent Accounts
There is no shortage of alternative finance companies, such as those who provide short term loans. Fraudsters can successful open accounts in another individual’s name, using a combination of SSNs, fraudulent gas statements and other personally identifiable information (PII). Individuals should be extra vigilant for any evidence of accounts being opened in their name.
Carding
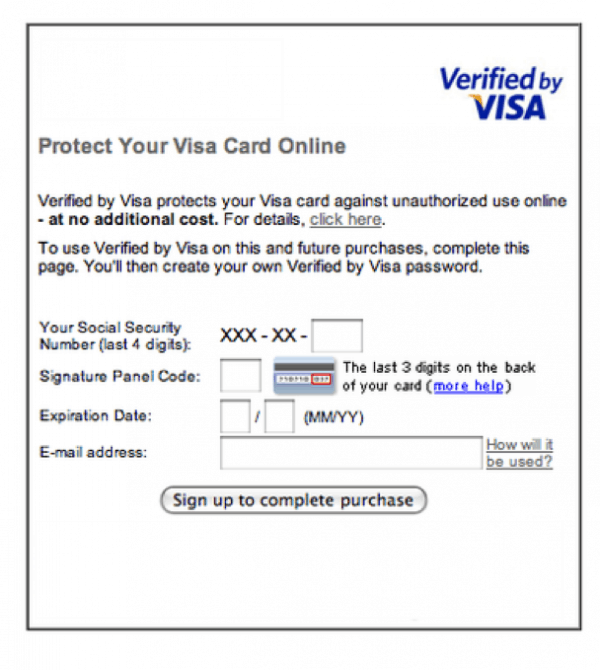
PII is valuable to payment card fraudsters, who require such information to bypass security controls such as “Verified by Visa”, which sometimes ask for digits of cardholders’ SSNs. There are plenty of high-quality cards that criminals use which do not require extra validation, but the lower-level carders must turn to SSNs to enrich lower-quality card dumps. It’s important to remember that SSNs and payment card fraud are inextricably linked.
An example of a security control for online credit card payments
Benefits Fraud And Medical Care Fraud
Although less glamorous than tax return fraud and carding, benefit and medical care fraud is a real risk. As with tax return fraud, this is hard to detect when it happens, but individuals can be vigilant when checking their Explanation of Benefits statement and flag any unfamiliar activity to their insurance provider.
Resale Of Data
It’s important to note that the individuals responsible for the breach are unlikely to be the same criminals conducting the day-to-day fraud. In the case of the Experian breach, this stolen data soon made its way on the (now defunct) Hansa marketplace. As I’ve previously mentioned; there’s already a market for SSNs to enrich credit card information, so it’s likely that many actors could end up getting a piece of the pie.
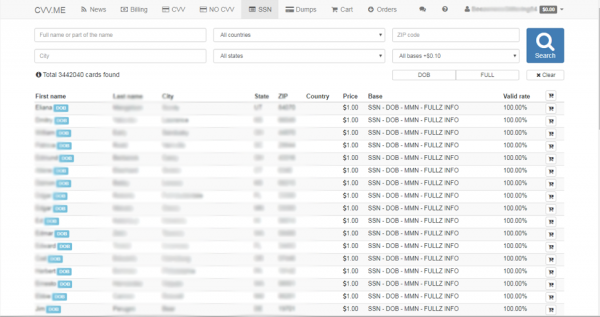
For lower level criminals, the expenses associated with criminal activities will get even lower. SSNs are already cheap; on one AVC (Automated Vending Cart) site (shown in Figure 3), there are over 3.4 million SSNs for sale at only $1. This includes full names, addresses, and – for a large number of accounts – dates of birth. In California alone, there were 334,000 SSNs for sale.
With tens (and potentially hundreds) of millions more SSNs potentially entering the market, the opportunities for criminals to commit fraud will increase and the price will decrease even more.
A screenshot of an AVC selling Social Security Numbers
So far, I’ve focused heavily on SSNs – but credit card information was also accessed. However, in the breach. While this number is hundreds of thousands (209,000), it is unlikely to have a significant impact on an already burgeoning black market for card credit information.
Enablement Of Nation State Campaigns
Although Equifax claimed this intrusion was conducted by a criminal threat actor, it is possible that this was a nation state actor. (Quick reminder to re-read my note from above “attribution is always a challenge.”) In the event that a nation state actor is responsible for the intrusion, then like the OPM breach, we won’t see the data being monetized in the criminal underground. The stolen data will be leveraged to enable nation states’ campaigns against their intelligence targets.
Enablement Of Hacktivist Campaigns
If we are going to consider nation state actors, we should also consider hacktivist threat actors and their activities around the stolen data. If hacktivists were responsible (I think this is a pretty unlikely scenario, let’s call it #OPunlikely) you could expect to see them use the data to target organizations and individuals that run counter to their world views. Embarrassment and dox’ing, hacktivist go-tos, would come into play.
WHAT ENTERPRISES CAN LEARN FROM THE EQUIFAX BREACH
- Incident response takes time and eradication in particular takes time. Equifax said that the intrusion was discovered on July 29th and that they “acted immediately to stop the intrusion.” Equifax’s goal was to contain the adversary that first day, but that true eradication took much longer. It is important that you set expectations with your leadership into how long eradication could actually take.
- 3rd party risks raise their ugly head once again. Some aspects of this intrusion remind me of the September 2015 T-Mobile breach. In this intrusion, Experian was hosting T-Mobile data that an unauthorized party accessed and this resulted in the loss of 15 million individual’s records. Any organization with a business to business relationship with Equifax needs to find out the scope of any potential loss of their employee or customer data. This 3rd party exposure also highlights the need for 3rd party risk monitoring.
- Crisis communication is key. Effectively communicating during an intrusion is important, it won’t absolve you of your sins, but doing it wrong could make the situation far worse. Understanding when and what to communicate is also important. Equifax discovered the intrusion on July 29th and notified on September 7th. Some might ask why did it take so long for the notification, but I don’t think that a month is that long. The investigation needs to be far enough along so that you can confidently communicate the situation. A CEO that comes out 2 days after a breach and then minimizes what is a much more significant threat will be performing a mea culpa in little time.
- GDPR will change the breach notification game. Now let me really trip you up, how would this situation play out if it was after May 25, 2018 and Equifax lost European Union citizen’s data? General Data Protection Regulation changes everything with 72-hour breach notification windows. GDPR states, “This must be done within 72 hours of first having become aware of the breach.” When the fines do come into place, the timing of the communication will have a significant impact.
WHAT CONSUMERS CAN LEARN FROM THE EQUIFAX BREACH
- Consider taking advantage of Equifax’s offer. Although the irony is not lost to me, taking advantage of credit file monitoring and identity theft protection offers is important. Check out equifaxsecurity2017[.]com for more. If you don’t want to use Equifax for these services, I get it, look for at alternatives with someone like Transunion or Experian.
- Be vigilant about your payment card activity. Use email/SMS alerts to notify of account transactions ($100) over and under ($5) a specific amount. If an unauthorized transaction occurs you can be notified immediately, and can quickly take action. Be vigilant about your card activity and alert your bank about any suspicious activity.
- Address tax fraud with IRS Form 14039. If you find out you are a victim of tax return fraud, there are still things you can do. Victims can file and send a IRS Form 14039. Further details are available here.
- Check your Explanation of Benefits (EOB) statement. It might look like another piece of spam mail, but it is important to reconcile the EOB statements that your insurance sends you. This your best bet to monitor for medical card fraud. Make sure to report any unfamiliar activity as soon as you observe it.
- Assume breach. In the corporate cyber security world, we have learned to “assume breach”. Consumers should also operate under the impression that their confidential data has been compromised.